Reduce false alarms by 95%
Our AI analyses over 2M alarm images a day and significantly reduces false alarms.
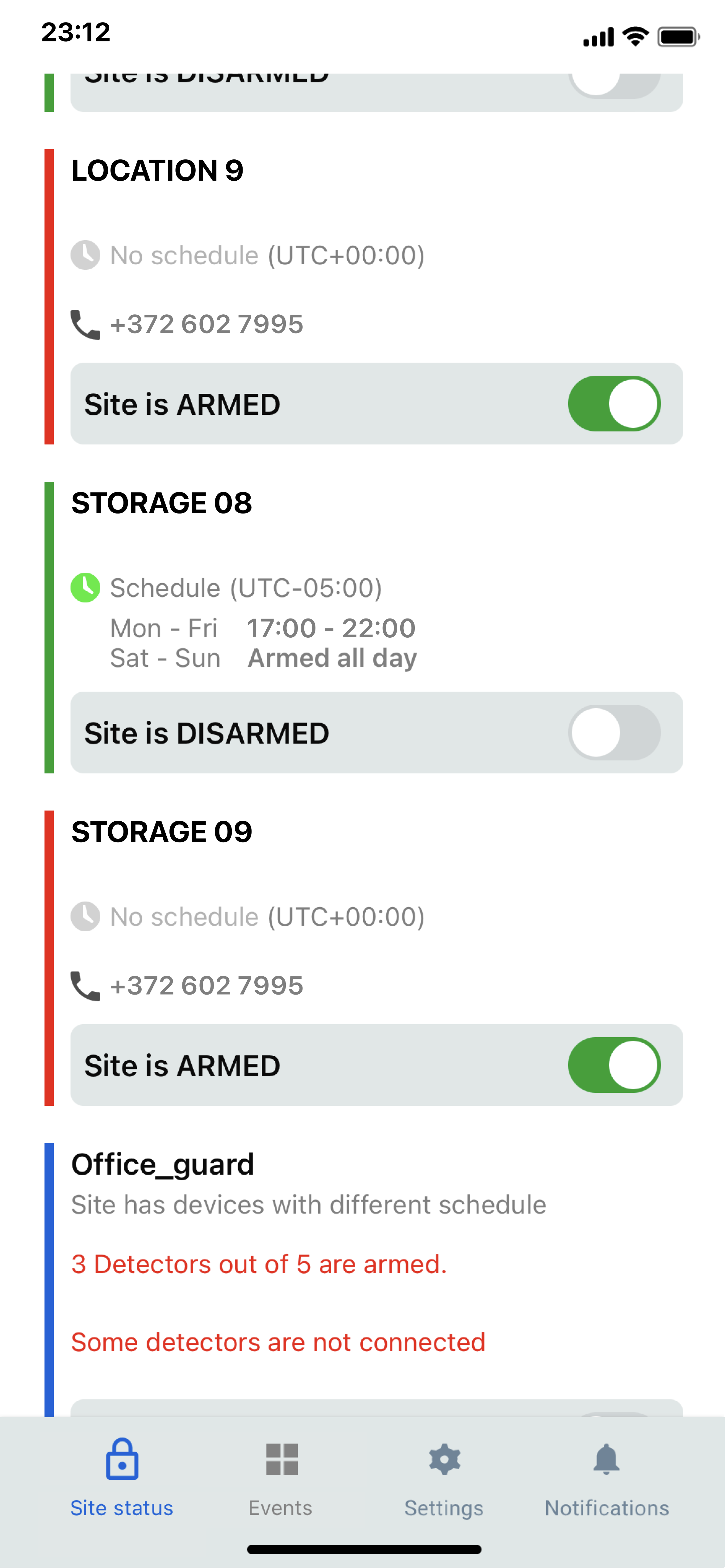
Manage devices remotely
Arm and disarm, manage schedules, and change settings from the desktop or mobile app.
Reconeyez cameras use mobile connectivity to send alarm images to the Reconeyez Cloud, hosted on our secure servers.
We use a world-class AI model to analyse millions of alarm photos across tens of thousands of detectors every day.
- Manage your security system remotely and take advantage of patented AI capabilities to extend battery life and reduce false alarms.
- If movement is detected, an alarm image is sent to the cloud
- The alarm image is stored securely and analysed by AI
- If a person, vehicle, or animal is found, an alarm is sent
Loud push notifications
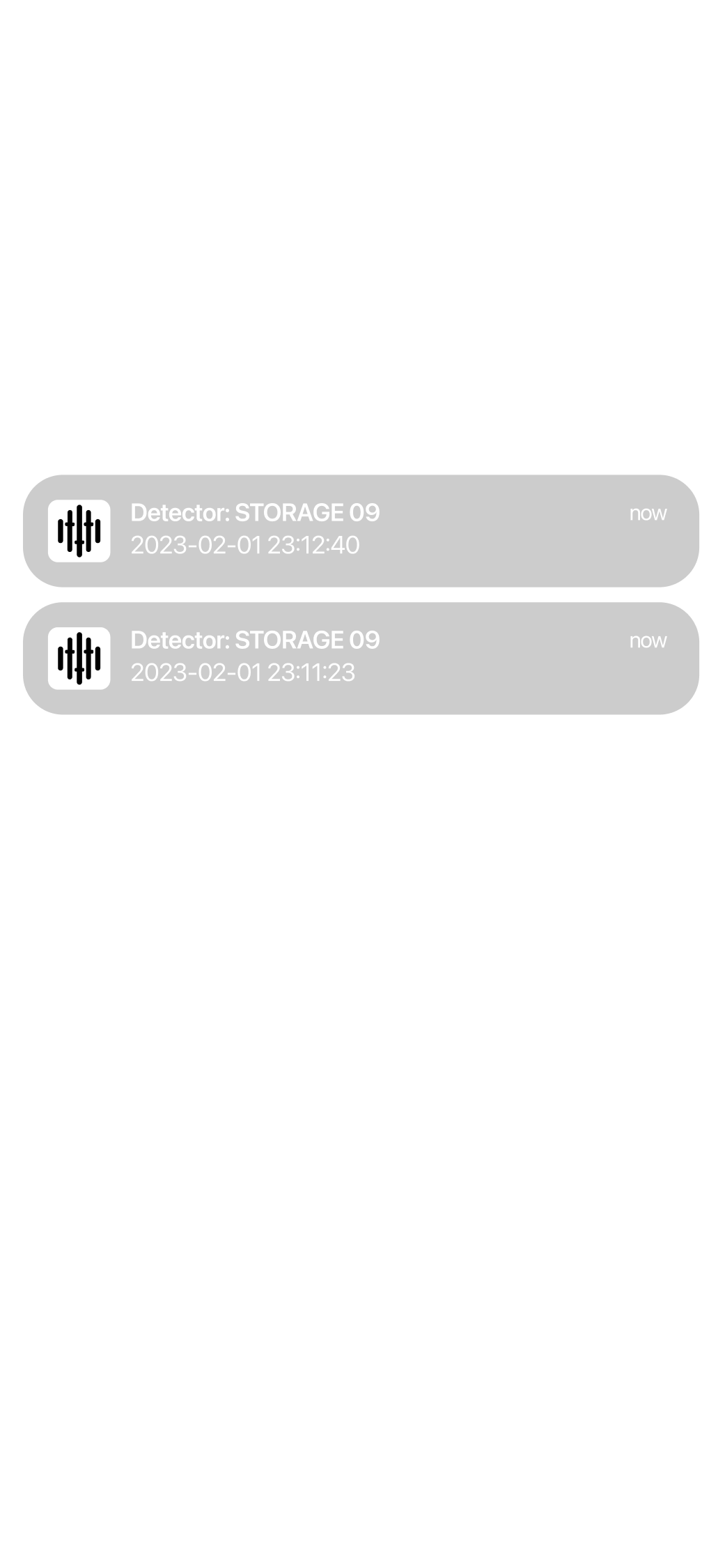
Receive alarm notifications together with photo descriptions
Access alarm images
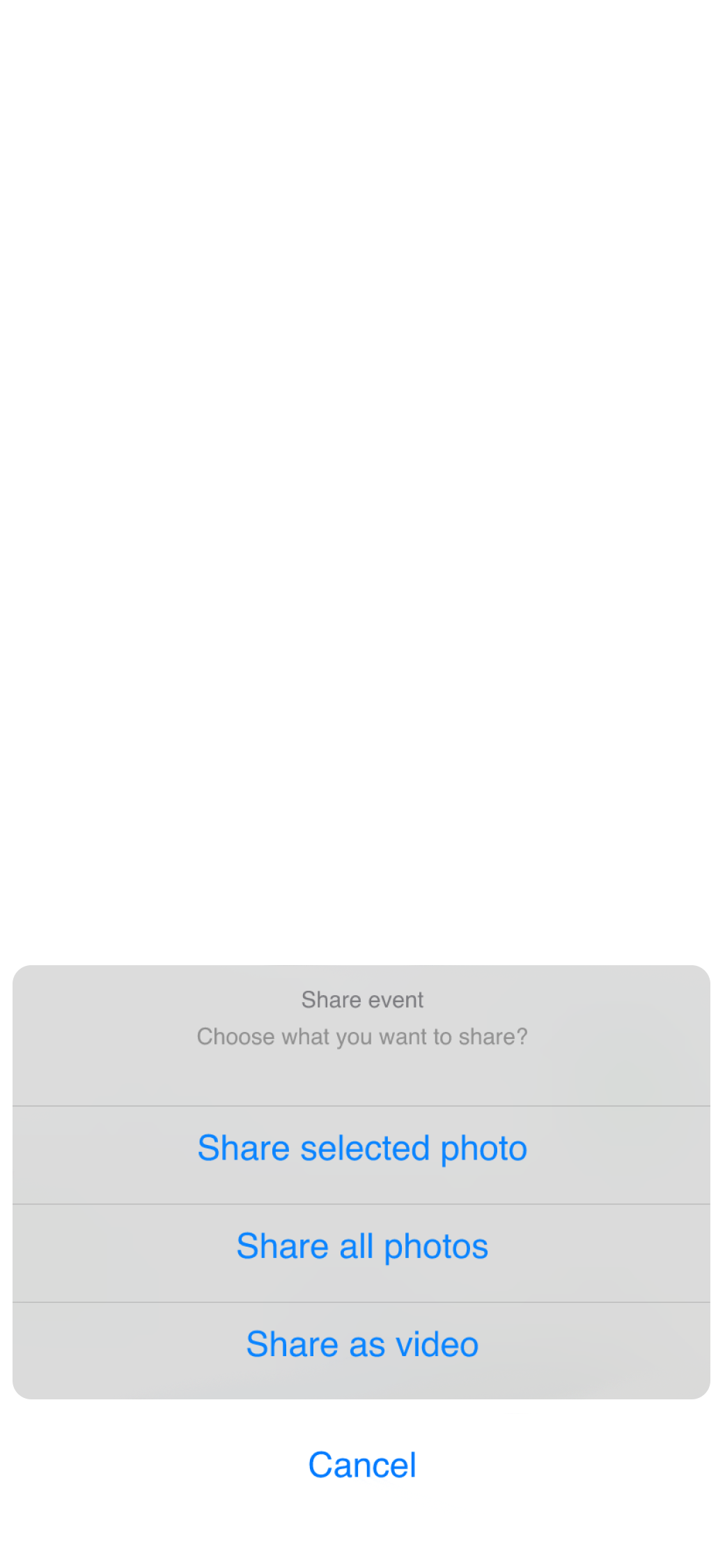
Access and share HD-quality alarm images instantly
Arm and disarm
Access and share HD-quality alarm images instantly
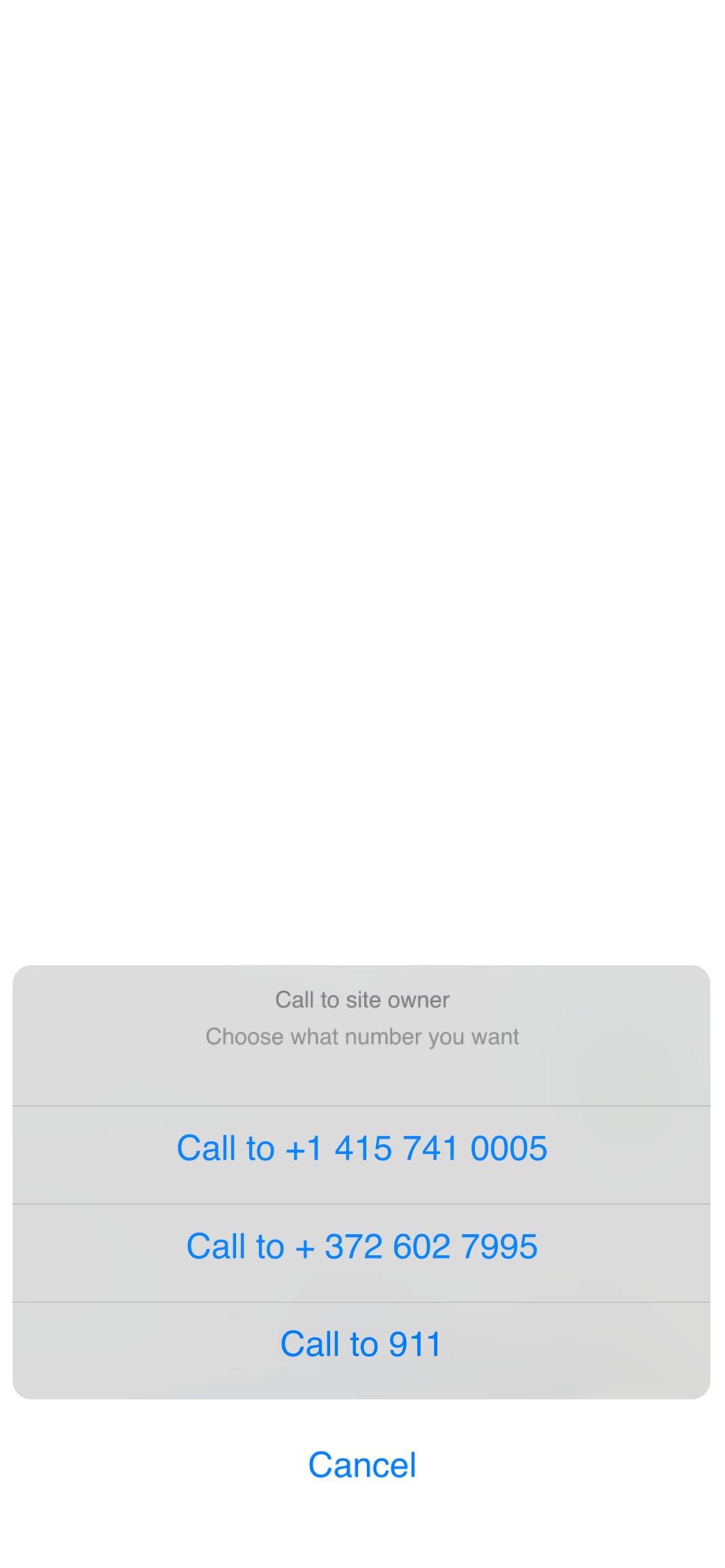
Activate the siren
Verify the alarm image and activate the siren


Arm and disarm
Access and share HD-quality alarm images instantly
Activate the siren
Verify the alarm image and activate the siren





